Coronium.io: Mobile Proxy Marketplace Review
Blog » Coronium.io: Mobile Proxy Marketplace Review
If you buy proxies to 💰 make money (not just “have an IP”), you care about three things: success rates, account longevity, and cost per successful action. Coronium.io is a mobile proxy marketplace built to optimize exactly those levers – real 4G/5G carrier IPs, device-level isolation, and battle-tested rotation controls so your profiles live longer.
Use HTTP/SOCKS5 inside 🚀 Dolphin Anty profiles for per-profile isolation and quick rotation; optionally layer a system-level OpenVPN tunnel for cases that benefit from encrypted, carrier-grade routing (e.g., streaming, real-time apps). Coronium.io provides 📱 mobile proxies over HTTP(S), SOCKS5, and OpenVPN so you can choose the right rail per task.
Below is a straight, ROI-oriented overview you can publish as a value article (not a hypey advertorial).
What Coronium.io is and Why it’s Different
A curated mobile proxy marketplace of real 4G/5G devices. Every port maps to an actual modem/SIM on a mobile network (no recycled DC subnets, no sketchy tunnels). You get:
- Real carrier IPs (per device), naturally high-trust across most platforms.
- Device isolation (no IP sharing roulette).
- HTTP(S), SOCKS5, and OpenVPN access:
- SOCKS5 supports UDP relay (client-dependent) for apps that need it.
- OpenVPN preserves UDP/QUIC/HTTP-3 semantics end-to-end and adds a strong encryption layer to be not detected as proxy.
- Rotation & stickiness controls that match how platforms actually score risk (predictable session lifetimes, human-like resets).
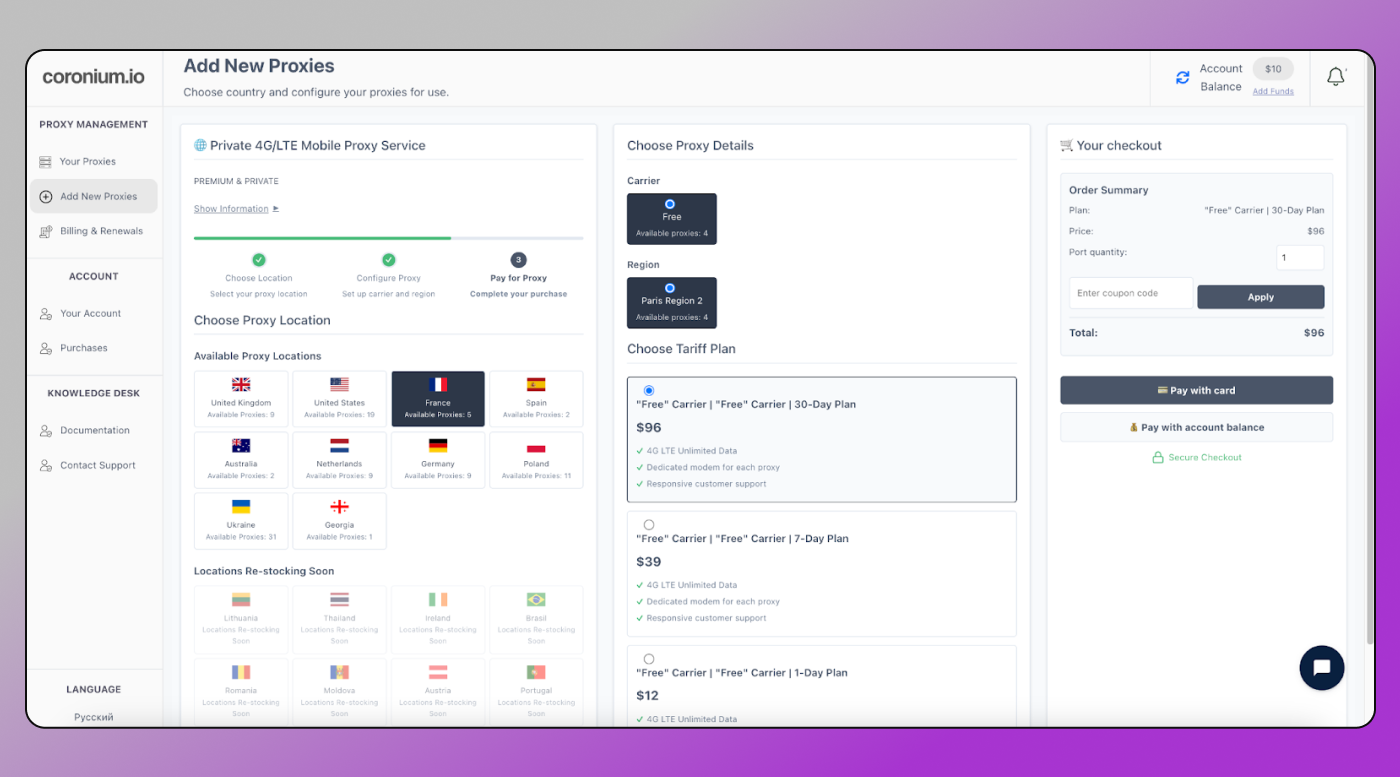
- Global GEO & multi-carrier coverage 15+ countries
❗ Result: fewer bans, fewer puzzles, longer-lived identities → lower cost per verified account, checkout, or data row.
Why Mobile IPs feel “Cleaner” in Practice
Platforms weight “real-user” signals. Mobile ASN ranges and NAT’ed pools often look like normal consumers, not server farms. Combine that with:
- Carrier diversity (Telco reputation > DC blocklists).
- Freshness via rotation (session resets that mimic user churn).
- One-device-one-identity discipline (no cross-contamination).
- A lot of other people can be using same IP for regular things of like browsing amazons and just real usage (real users in the area)
You’re aligning with the traffic shape anti-abuse systems expect to see – that’s cleanliness in an operational sense.
❗ Important: “Clean” doesn’t mean “invincible.” It means higher baseline trust so good ops (browser fingerprints, timing, content quality) can do their job.
The Clean-IP Framework: How Coronium is Eengineered for Trust
1) Supply integrity
- Real modems/SIMs, vetted farmers, monitored uptime.
- No recycled “mystery” hosts; clear device → port mapping.
2) Rotation policy that mimics humans
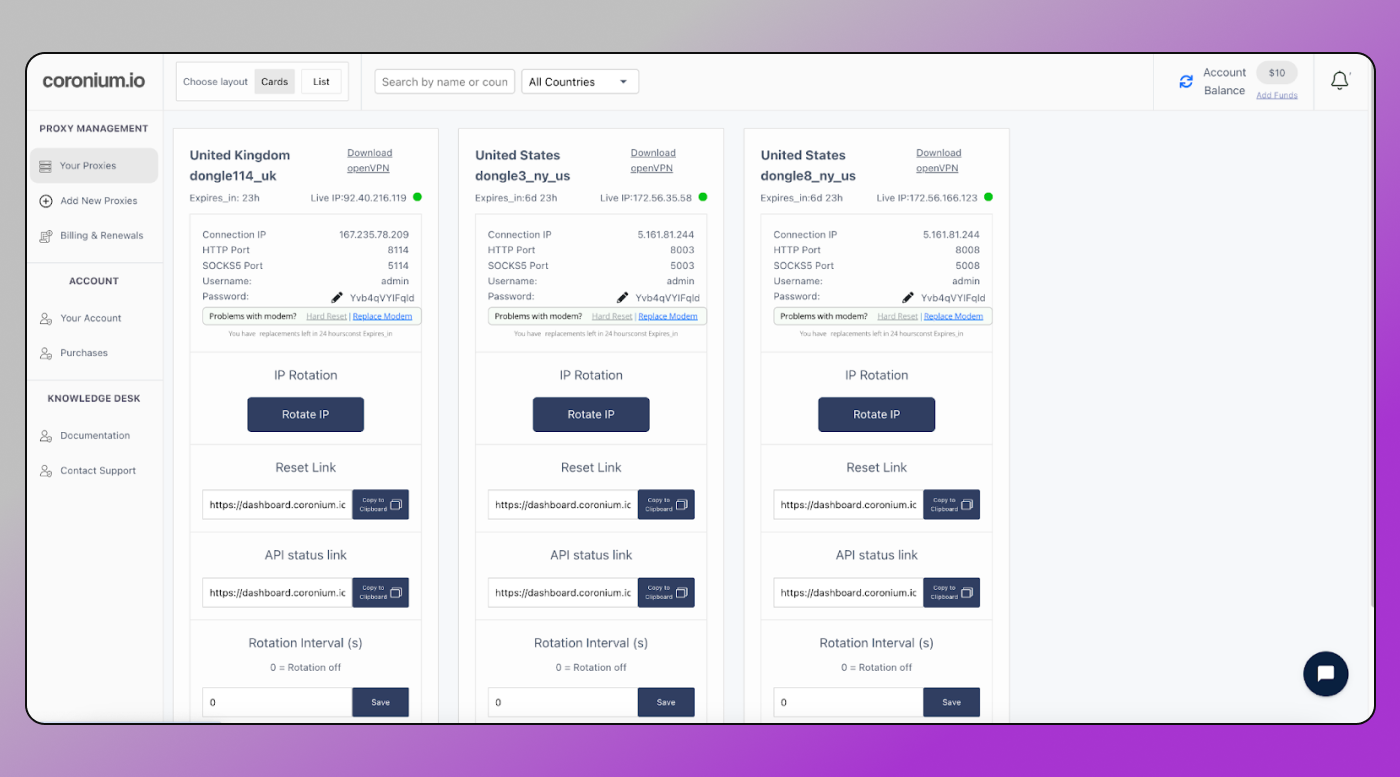
- You control IP stickiness (60 sec is minimum rotation, it goes down for 10 seconds when you rotate).
- Hard resets that actually change eNodeB context when needed (not just a port shuffle, actual device connection on/off to get new IP assigned)
3) Protocol choice for your workload
- HTTP/S & SOCKS5 at the app (browser) layer for per-profile isolation.
- OpenVPN: at OS layer when you need mobile residential VPN for better isolation. Least detected way to use proxies..
- SOCKS5-UDP available for clients that truly use it (note: alot of browsers fall back to TCP under a proxy; test your app).
4) Tooling & support for scale
- Dashboard + API for port lifecycle, geo swaps, and metering, simple billing and no auto subscriptions for convenient and fair usage – renew how you need and when you need.
- Helpful support via Telegram @coroniumio or live chat on site or email (slower for email).
Fingerprint Coherence: High-Level Best Practices
When using antidetect browsers with proxies 🤓 keep in mind these things:
- Geo + Time + Language: Keep these aligned (e.g., DE IP, Europe/Berlin timezone, de-DE UI).
- Hardware class: Don’t spoof a low-end iGPU as a workstation-class GPU.
- WebRTC: Prefer controlled handling (not leaking LAN IPs that don’t match your story).
- Canvas/Audio/Fonts: Consistency beats “random.” Aim for plausible, not exotic.
- Session pacing: Human-like intervals, realistic error tolerance, and breaks.
Quick integration
Dolphin Anty / multi-account browsers
- Add HTTP/S or SOCKS5 per profile for identity isolation.
- If your app needs UDP/QUIC (SOCKS5 can also work) or you want an encrypted mobile tunnel: connect OpenVPN at the OS level, then run profiles (proxy-over-VPN works too).
Headless & programmatic
- Use SOCKS5 for wide client support; if your client supports UDP ASSOCIATE, you can push UDP flows (verify end-to-end).
- Prefer OpenVPN(UDP) for protocols that truly require UDP fidelity.
FAQ for the Pragmatic Buyer
Do I get static IPs?
You get sticky sessions tied to a real device. Static-for-ever isn’t the goal in mobile; predictable stickiness windows are (and they’re better for longevity).
Can I pass QUIC/HTTP-3?
Yes, via OpenVPN or SOCKS5-UDP can work if your client truly supports it, but most browsers disable QUIC when a proxy is set. For browsers, use OpenVPN if QUIC matters.
Is this compliant?
Coronium is for lawful, ToS-compliant use (ad verification, QA, research, brand protection, etc.). You’re responsible for how you use it.
Will this fix everything?
No proxy solves bad ops. But clean mobile + sane fingerprints + human-paced flows is the winning stack.
Getting Started
See tutorial how to buy coronium mobile proxies here: coronium.io/buy-mobile-proxies
The Takeaway
If proxies are a cost center, clean mobile turns them into a profit lever: better trust signals → longer sessions → fewer resets → lower CPA. Coronium.io’s marketplace model (real devices, protocol choice, rotation discipline) is built for operators who track results, not just IP counts.