Which Plugins Blow Your Cover in an Antidetect Browser
Blog » Which Plugins Blow Your Cover in an Antidetect Browser
You can use the best antidetect browser in the world, configure your fingerprint perfectly — and still 🔎 get caught by antifraud systems. Why does that happen? It’s simple: there are 🧩 browser extensions that can deanonymize you. What are these plugins and how can you use them without compromising your anonymity? Let’s dive into the topic.
VPN Extensions
Using 🔗 proxies — not VPNs — in an antidetect browser is a golden rule. But just in case, here’s a reminder why you should never use VPN services through an antidetect setup.
Virtual Private Network isn’t a red flag for many antifraud systems as a lot of legitimate users rely on it. However, VPNs can leak your real IP and 🌏 location.
![]()
Antifraud systems always see your exact time zone and language settings — not what the VPN is showing. All key data leaks through VPN and the system can easily detect that all browsers are being used by one and the same person.
Crypto Wallets
These include 💲 Metamask, Trust Wallet, Phantom and other extensions for accessing crypto accounts. Crypto wallet plugins collect the following data:
- IP address and geo;
- Time zone;
- System settings (OS, deviceMemory, hardwareConcurrency);
- WebGL, Canvas and AudioContext;
- UI behavior (signatures, logins, wallet addresses);
- Local environment and call history (e.g., which sites requested wallet access).
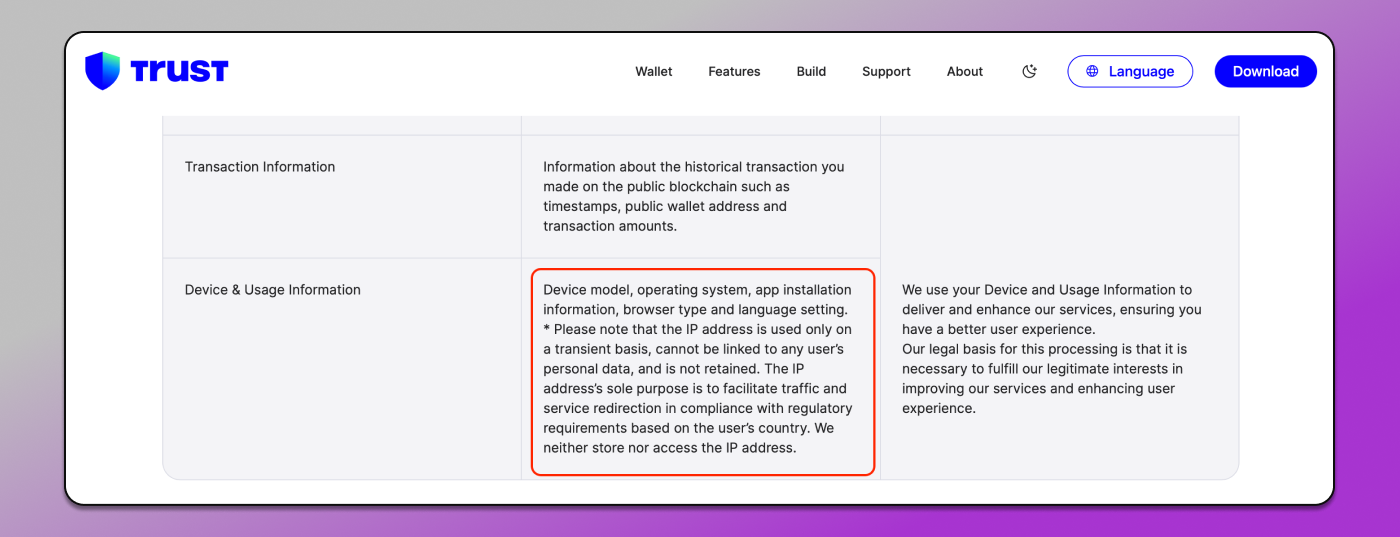
Example of data collected by Trust Wallet.
When logging into crypto platforms, the wallet passes to the site window.ethereum.address which is a special property used for wallet operations.
The most 🎦 common deanonymization scenario is as follows:
- You launch a browser profile with a crypto wallet plugin;
- The plugin connects to a dApp (say, OpenSea or Uniswap);
- You log in with a password or seed phrase;
- The extension logs your system fingerprint, IP, public wallet address and your activity.
Now, if you log into the same wallet from another browser profile, the dApp site will quickly realize that the same wallet is being used in two “different” environments. The fingerprint is different, the IP and geo might differ as well — but the window.ethereum.address is still the same. Antifraud systems detect this inconsistency and may restrict or even ❌ block your access. No antidetect tool can spoof window.ethereum.address to bypass this.
Grammarly
This is an AI-powered plugin for ✍ spell checking and text generation.
Sounds useful, right? So how can it blow your cover? Grammarly is integrated into some websites via SDK or partner programs. Platforms like Shopify, eBay and Amazon use it heavily.
Grammarly 🙋♂️ captures user behavior, language, typing speed, keyboard layout and geo. It also collects:
- Device OS;
- Language settings;
- Time zone;
- Screen resolution.
- ОС устройства;
Deanonymization can happen in two ways:
- Data mismatch. Your antidetect shows one fingerprint, but Grammarly (if you’re logged into an old account) sends another. For instance, geo via IP is 🇺🇿 Tashkent, Uzbekistan, system language is 🇷🇺 ru-ru, but your antidetect setup says 🇵🇱 Warszawa, Polska, and language is polski. This inconsistency draws attention and may trigger extra checks.
- Launch time of different profiles. If Grammarly sees users with 👯 identical behavioral patterns showing up in multiple browser profiles at the same time, it might relay this info to a website.
Loom, Zoom, Notion Web Clipper…
These plugins help with 📹 video recording — either from webcam (for video calls) or screen (e.g., to capture user actions).
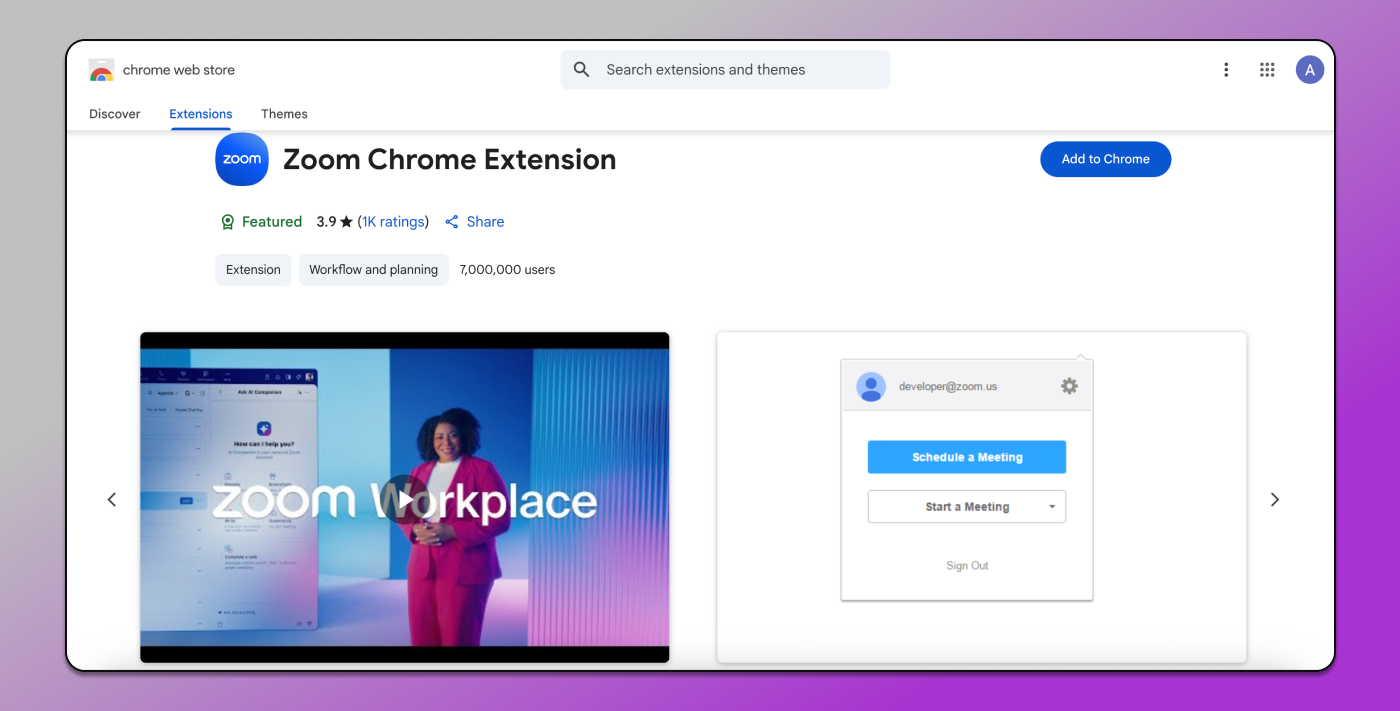
They require real access to the device and OS. That means they go beyond the browser, tapping into system data like screen, camera, file system, clipboard, etc. So even if you’re using an antidetect, they can see the real OS and hardware.
Here’s an example of the data collected by the Zoom plugin.
Even when using an antidetect, you’re giving these extensions ⚙️ access to real system parameters, which might contradict with what the antidetect is showing. For instance, if your Canvas/WebGL doesn’t match your screen resolution, that’s a trigger.
Some screen recording extensions (like Notion Web Clipper) also get access to the clipboard and even file system. This is a direct path to deanonymization — different browser profiles, same physical device.
All this becomes 🚨 a loud signal: “same user, different screens, languages and fingerprints mean multi-accounting”. And what is the worst part? These plugins may send data to websites belonging to third parties. Loom, for instance, allows embedded videos with analytics and the Telemetry ID can be sent via iframe or API request. Zoom SDK might be built into other sites (like corporate portals), sharing telemetry with site owners.
If you’re logged into an extension (e.g., Zoom or Notion) and later visit another site with embedded SDK — that site may recognize you, even in a different browser.
Affiliate Plugins: Ads Trust, Meta Pixel Helper, Ad Library Cloud
These plugins don’t send any real device data or conflict with any fingerprint parameter. But antifraud systems have learned to recognize them as 🛠 core tools of fraudsters. This especially applies to extensions used for affiliate marketing on Facebook, TikTok and Google.
The same can be said about the tools used by fraudsters on marketplaces and betting platforms.
If antifraud systems spot similar behavior across your browser profiles, having these extensions installed only increases its suspicion.
Ad Blockers: Adblock, uBlock Origin…
Ad blockers interfere with script loading, DOM structure, and browser behavior. That’s not a problem, but if your fingerprint already has some inconsistencies, using a blocker amplifies them. That could alert antifraud algorithms.
For example, if they notice a mismatch between your GPU, OS version and video loading speed, they might perceive it as a device feature. But blocking analytics scripts plus other inconsistencies is a trigger for fraud detection systems.
What to Do About It
These tips for staying anonymous naturally follow from the points above.
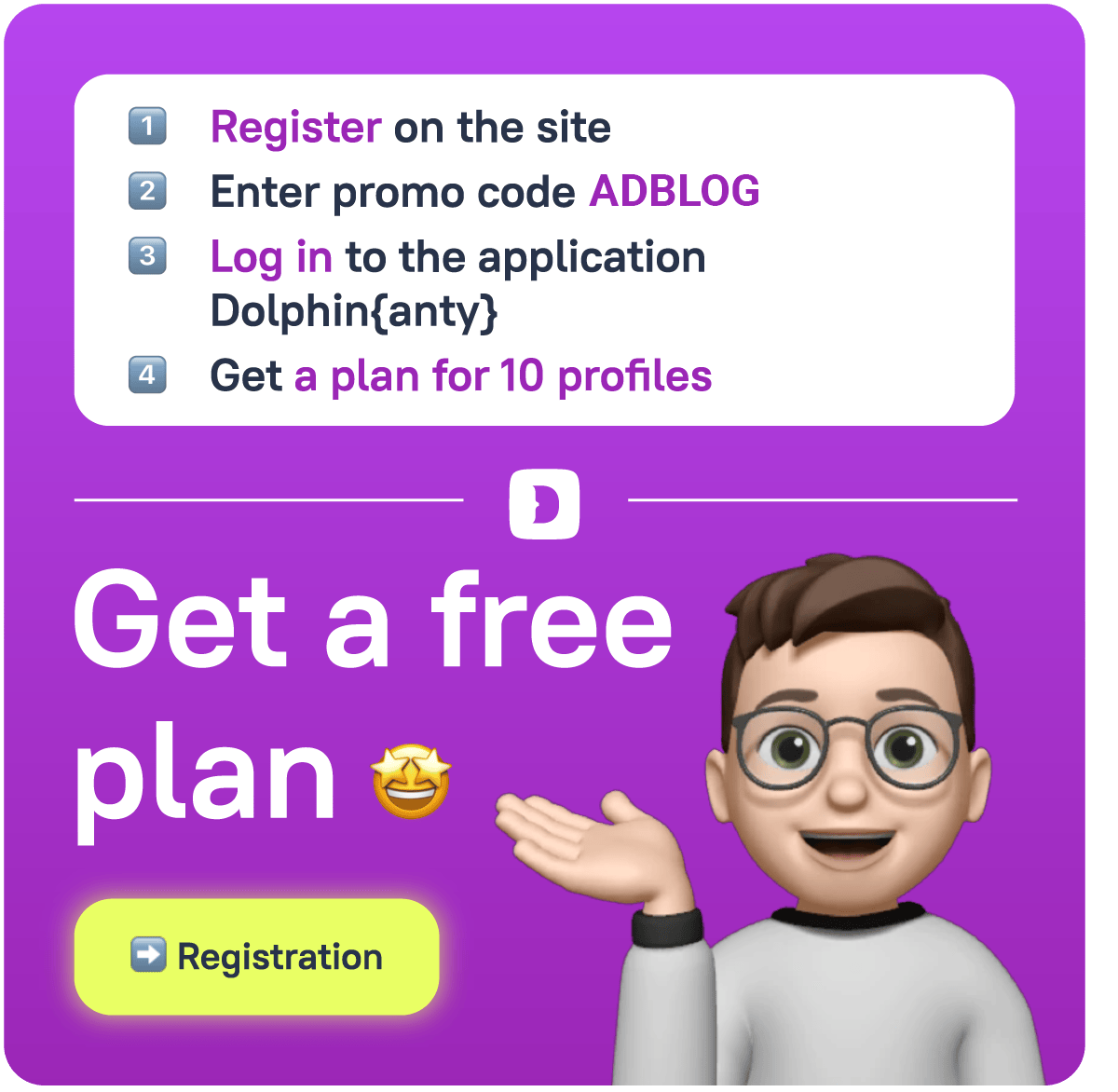
☝️ Don’t use VPNs at all. You can install them in some browser profiles just to mimic typical user behavior. But never turn them on — always use the recommended proxies. Some antidetect browsers like 🚀 Dolphin Anty have a special section with proxies perfectly suited for their multiaccount environment.
✌️ Avoid using crypto wallets, Grammarly, Zoom and other plugins with device access in antidetect profiles. Just don’t use them at all on devices involved in multiaccounting. But if that’s not an option, only log into these services via your regular browser — not the antidetect one.
🙌 Affiliate plugins and ad blockers — don’t install them right away. Let your account get used to them after logging in from a new profile. Add these extensions only after some time.
By following these simple rules, you’ll significantly reduce the risk of deanonymization and extend the lifespan of all your accounts.