The main mistakes affiliates make when using anti-detect browsers
Blog » The main mistakes affiliates make when using anti-detect browsers
After starting to use anti-detect browsers, some affiliates face problems. For example, social networks instantly ban their accounts, the digital fingerprint doesn’t look unique, etc. As a result, they think that all this happens because of incorrect work of the anti-detect browser. In fact, most often the problem is in the actions of the affiliates. Below, we’ve collected the main mistakes and explained how to avoid them.
⛔️ Mistake #1: To use one proxy for multiple accounts at once
What’s wrong. — Some affiliates use one IP address for several accounts and browsers at once.
What it leads to. — Anti-fraud(security) algorithms of traffic sources see that the same data is used in different accounts and conclude that they are connected. If one of the accounts breaks the rules of the website, all other accounts will also get suspected or even blocked.
What to do. — Use a separate IP for each account. The same goes for phone numbers, emails, pay cards, etc. If you have unique data for each account, the risk that the traffic source may find a connection between the accounts will be much lower.
❗️ Mistake #2: Wrong proxy is being used
What’s wrong. — Some affiliates buy cheap proxies or even use free ones. This is often done by beginners who have a limited budget.
What it leads to. — The IPs of cheap proxies are often already blocked and included in the ban list of the largest traffic sources: search engines, social networks, etc.
What to do. — Although there are users who have been working with cheap proxies for years and haven’t been banned, these are rather exceptions. For affiliate marketing, use mobile and residential proxies. Read more about it in our article on how to choose proxies for an anti-detect browser.
🙅🏻♂️ Mistake #3: Not using proxies at all
What’s wrong.— The affiliate creates a fingerprint in the anti-detect browser without proxy.
What it leads to. — Although the fingerprint of the browser and the device change, the connection and location information stays the same. You can verify this by conducting a simple experiment:
- Open pixelscan in your normal browser and anti-detect browser profile without changing your IP(using proxy).
- You will see that your browser and operating system settings may be different (in blue), but the IP will be the same (in red):
Print screen from Google Chrome browser without using a proxy
Print screen from Dolphin{anty) browser without using a proxy
Because of this, the website’s security algorithms bind all accounts that have the same data. This leads either to instant blocking, or it will happen in the future when one of the accounts violates the policies of the website.
What to do. — To make sure your digital fingerprint doesn’t match other accounts, use proxies. Some affiliates say they use the simplest Datacenter proxies and work for years without bans, but that’s more of an exception. As we’ve written before, better use mobile and residential proxies.
💢 Mistake #4: Trying to use the anti-detect browser during crashes and bugs
What’s wrong. — Trying to add new data to accounts, launch advertising campaigns, and basically trying to work with anti-detect during a crash or attack.
What it leads to. — At best, you just can’t get into anti-detect, at worst — you can loose your account.
What to do. — We timely notify you about all the news and updates of Dolphin{anty} in our Telegram channel.
For example, on February 17, the day of sales on Coinlist, our anti-detect browser Dolphin{anty} was attacked. Because of this, some users had trouble with working for several hours. Although the problem was not our fault, we automatically charged all users an extra free day for the inconvenience:
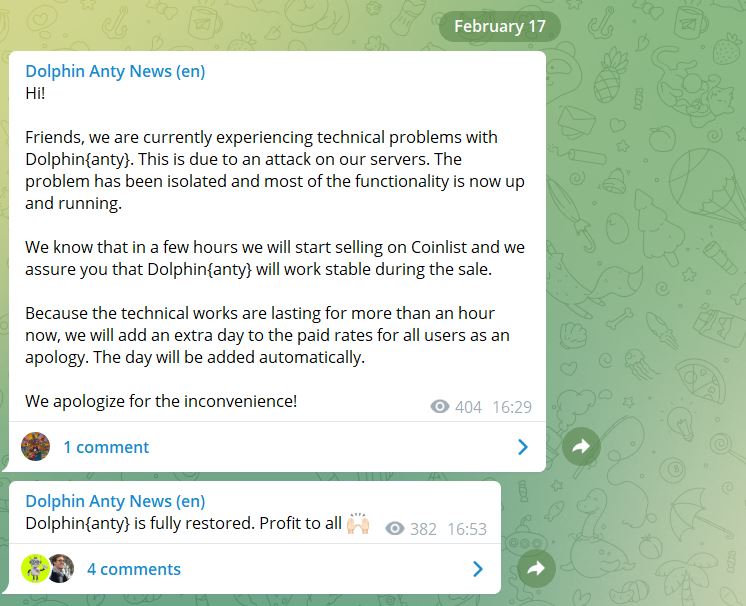
Report of a recent attack on Dolphin{anty} servers
Subscribe to our news channel, and you will always be aware of all news and updates.
⭕️ Mistake #5: Trying to set up individual parameters of the fingerprint manually
What’s wrong. — In Dolphin {anty}, the user can get a ready digital fingerprint in one click or set up the parameters of the fingerprint manually. Some affiliates are guided by unverified recommendations on the Internet and manually change the parameters of the fingerprint.
What it leads to. — Some parameters might not look realistic and the security algorithm of the website will suspect that this is not a real user. This can lead to a ban of the account.
What to do. — We do not recommend setting up a digital fingerprint on your own, unless you know for sure how different parameters relate to each other. The fact is that each setting that goes into a digital imprint is combined or even related to other settings in a special way.
If you set them up incorrectly, you might get a fingerprint that anti-fraud systems will immediately figure out that you are hiding your real fingerprint. Given that the Dolphin{anty} anti-detect browser uses only the digital fingerprints of real users, our fingerprints will definitely pass the anti-fraud systems: no need to change them.
😒 Mistake #6. Using incorrect user-agents from purchased accounts.
What’s wrong. — When selling an account, most often, the seller gives the buyer cookies or user-agent. This is done to allow the buyer to use the account without entering the username and password: this reduces the risk that the website’s security systems will see that another person is trying to log in to the account. But sometimes it happens that the seller gives the wrong information.
What it leads to. — The website’s security system sees right away that the data isn’t correct, and blocks the account.
What to do. — Buy accounts from trusted shops with a guarantee on accounts. Such stores are also not protected against human error, but if there is a problem, you will easily get a new account within the warranty period. If you buy accounts from private sellers, there’s a chance that there is no warranty, and nobody will replace you anything.
😤 Mistake #7. Choosing a different OS in the digital fingerprint
What’s wrong. — Sometimes affiliates create an account and browser profile on one operating system(OS), but specify a different one in the fingerprint. For example, the account was created and will run on Windows, but in the fingerprint you see macOS.
What it leads to. — When checking the system settings, anti-fraud systems of the website may notice that although you have a macOS digital fingerprint, the fonts are actually from Windows. Because of this, the account gets suspicious or even blocked.
What to do. — Alas, so far, no anti-detect browser can 100% solve font problems.
The thing is that each operating system has two kinds of fonts: general and system fonts. General fonts are, for example, Arial, Times New Roman, Verdana, because they are available on all operating systems. But the system fonts are unique. For example, macOS has its own special system font BlinkMacSystemFont, which is not in Windows.
As a result, when you create a profile on a Windows device with a macOS fingerprint, security systems see that the fonts don’t match.
There are several ways to solve this problem:
- Create digital fingerprints on the same OS on which the account was created and with which you will be working. If you work in a team, ideally, all users should have the same operating system. For example, if you have Windows OS and that’s the same OS you’ll be using for your account, specify Windows in the fingerprint as well.
- Use Linux. Install Linux as a second operating system and download to it all the available fonts for macOS and Windows. Then set up those fonts and form your fingerprint with that particular OS. The point is that Linux is a more flexible system, so by downloading all sorts of fonts into it, you reduce the risk that security systems will find out, that you are trying to mask your fingerprint.
And lastly…
There’s another parameter that can lead to account problems in some cases: WebRTC.
What’s the point. WebRTC (Web Real-Time Communication) is the technology by which audio and video calls are transferred between different devices. Often when setting up a digital fingerprint, users choose to change WebRTC.
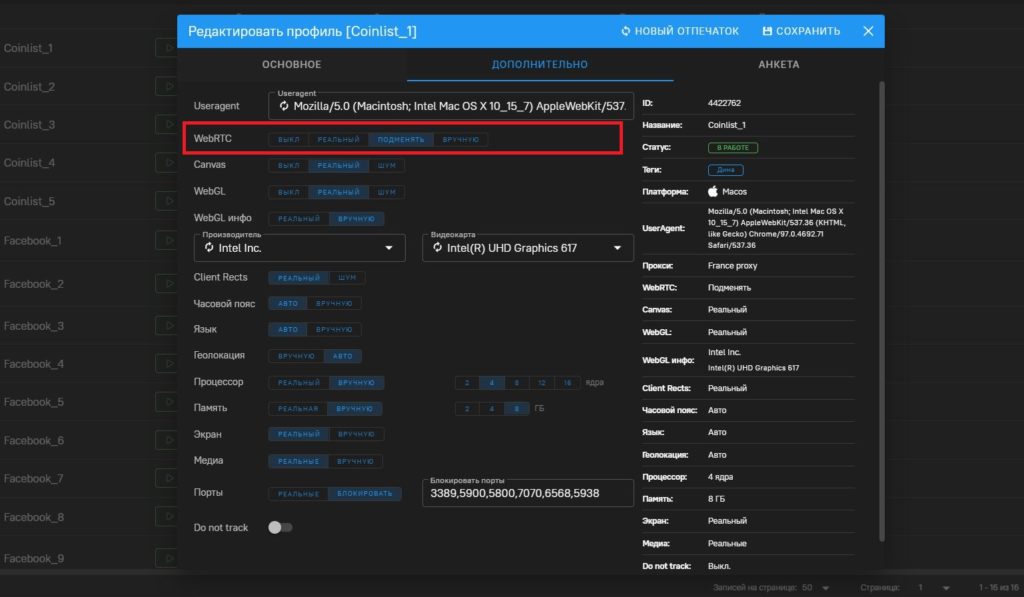
What this leads to. — Some anti-fraud systems see that the person is using a proxy in the WebRTC data. As in all other cases, this can lead to unnecessary attention from the traffic source and, in the long run, to account blocking.
What to do. — There is no definite answer. Some affiliates alter WebRTC, and they work without any problems with traffic sources. As an option, you can disable the transmission of WebRTC data when configuring a fingerprint. However, in this case, the source of traffic may become more suspicious about you, since ordinary users usually do not do so.